
The onrush of e-commerce has made online retail websites attractive targets for hackers, spammers, and cybercriminals of all shades. With hackers’ methods becoming more sophisticated and destructive, and the number of companies affected growing exponentially, businesses have to develop strategies to protect their assets against cyber threats.
From compromised data and financial expenses to leaked trade secrets and ruined customer trust, even a single vulnerability can lead to incommensurable damage and dig into crisis even a prosperous company.
We’ve created this guide based on the unique expertise that we got within 8+ years of working with eCommerce companies and, in particular, with Magento projects. However, the issues that plague online stores, as well as the practices contained in the article are also relevant to e-commerce websites run on other platforms: Shopify, Prestashop, Joomla, OpenCart, WooCommerce, and others. Every issue in the guide can potentially turn into a huge problem if things go wrong. So, we urge you to treat them seriously and fix them as soon as possible. Look at Shopify vs WordPress “battle” in ecommerce web building if you still think what is more secure.
The Most Common E-commerce Security Threats
There are lots of threats you need to protect your online store against. But we’ll touch on five the most common ones that plague retail and e-commerce businesses.
-
DDoS attacks
DDoS attacks disrupt servers with tons of traffic until they are unable to serve legitimate requests. To execute this attack, hackers use specific applications such as LOIC (Low Orbit Ion Cannon) to overload servers with HTTP, TCP, UDP packets.
A successful DDoS may result in lost revenue along with reputational damage due to enduring downtime. Besides, in some cases, a small denial of service attack can serve as a cover for data breaches.
-
Ransomware
Ransomware is a kind of financial fraud that turns out to be a full-scale business model for cybercriminals. Once a victim opens up a malicious email or visits an infected website, a cryptoworm is disseminated across the system and encrypts the victim’s files locking it out. The hacker demands a ransom from the victim to restore access to the encrypted files upon payment. The attack doesn’t require solid coding skills to be executed so that the number of companies affected is growing.
Here is the WannaCry ransomware message that has appeared in lots of computers running Windows XP systems across the world. The WannaCry attacks were a global epidemic that took place in 2017.
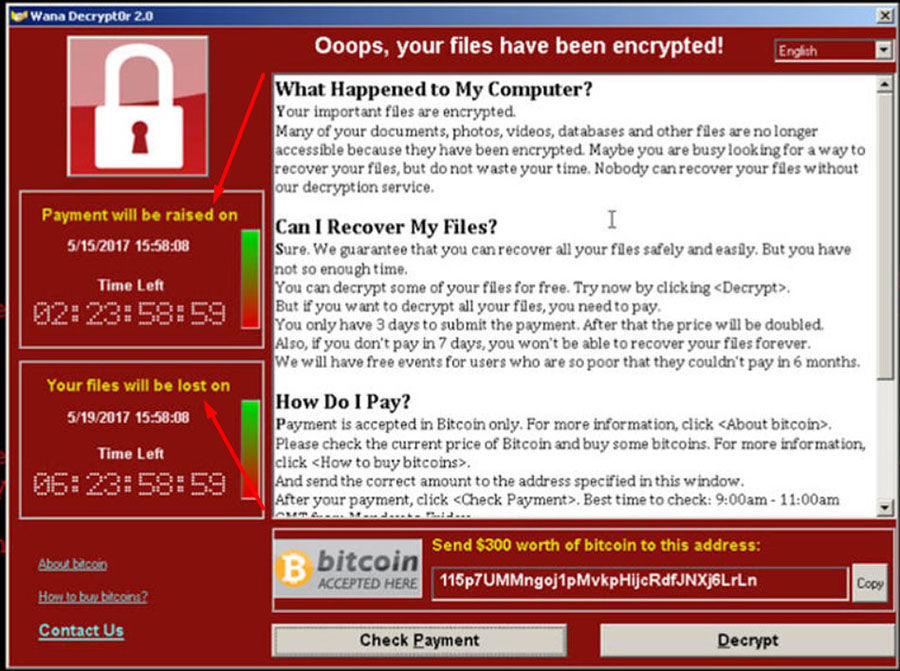
-
SQL-injections
The main targets of this attack are databases of websites and applications. Hackers insert a query with a malicious code leveraging vulnerabilities in the back-end. The query is treated as valid and executed. Once it happened, the attacker gains control over the website’s database. There are only a few rooms for a SQL-injection to worm its way into databases: through known bugs in a CMS/third-party modules, and via security loopholes in custom code. The last one may be caused by the work of a ham-handed developer. As such, we strongly recommend hiring experienced developers with strong expertise in creating e-commerce projects.
-
Malicious bots
Bad bots are self-propagating malware that is created to perform fraudulent activity leveraging security loopholes in websites. Thus, malicious bots can steal data, perform large-scale DDoS attacks causing downtimes, swoop up high-demand products, send spam, steal customers’ credentials, etc.
-
XSS (Cross-Site Scripting)
XSS is a security loophole that allows a hacker to compromise the interactions that a user has with an infected application. According to the latest stats, XSS is responsible for more than 31% of all cybercrime committed and is considered to be the #1 web attack, ahead of DDoS and SQL threats.
The Best E-commerce Security Practices
Implementing certain security practices can help safeguard the integrity of an online store, as well as the confidentiality of your clients’ data, minimize the risk of breaches, and keep to a minimum the consequences if any.
Scan Your Website For Malware
Detecting malware and finding out all security issues is an integral part of building fortifications around your store. The most actionable way to do so is by using a website malware scanning tool that checks for all types of malware and confirms through reporting.
The tool is free to use and is available from the Dashboard of your account. For detailed instructions on setting up and running the Security Scan Tool, read the official Magento documentation.
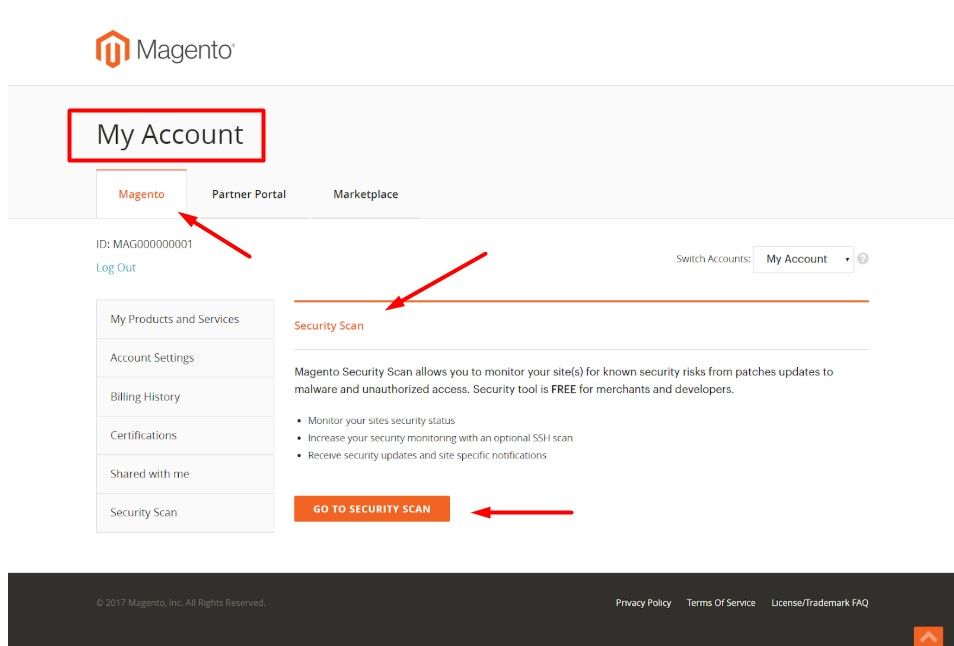
In order to set up the Magento 2 Security Scan Tool, you need to add your site in Magento Dashboard, verify its ownership, and then schedule a scan to run weekly, daily, or on demand.
We suggest choosing a period when your website experiences the lightest load for security scanning as the process can take lots of time.
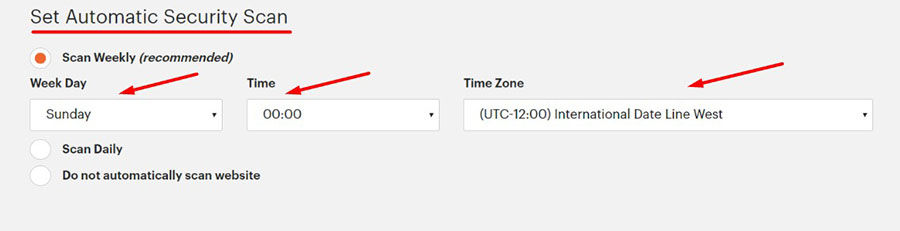
Choose the Week Day, Time, and Time Zone. By default, the scan takes place each day at midnight, UTC.
For e-commerce websites running on other platforms, you may use any tool for scanning websites for malware. Among the most popular ones are Sucuri, Web Inspector, SiteLock.
Make Sure All Your Payment Processors Are PCI Compliant
PCI compliance is essential for every business that collects, processes, and transmits sensitive information such as credit card data. As a business owner, you have to guarantee your customers a safe checkout. If a data leak occurs, your site can be suspended and frozen, not to mention fines that are getting progressively bigger the more damage your shoppers suffer.
PCI standards were created to ensure that a PCI-compliant processor provides strong protection to online payments.
Keep in mind that a processor can offer several tools that may have different security levels. For instance, PayPal Express Checkout is a PCI compliant payment system, while PayPal All-in-One is not.
Check this guide to PCI compliance for detailed information on how to make your payments secure.
Upgrade Your CRM to the Latest Version
As our experience shows, the vast majority of security loopholes caused by a delayed system upgrade. Typically, e-commerce platforms release a new version every three months. Those updates usually include bug fixes and security patches to protect stores against known vulnerabilities, so the best advice here is to upgrade your system as soon as a new version is introduced.
As for Magento, it is an open-source platform that allows anyone to see the code and leverage unpatched loopholes to penetrate the stores stuck on the older versions. So, if you can’t fix security issues for some reason, at least hide the Magento version you are currently using. To do that, you have to either delete or disable the corresponding module (commands are valid for Developer mode):

These commands will help you close information about the store for potential intruders and make the website more secure.
Employ 2-Factor Authentication
Using two-factor authentication to add an extra layer of security to the login process is a common practice for middle-sized and large e-commerce websites. Apart from a standard duo of a username and password, the method requires an additional code that is sent as an SMS to the user’s smartphone or email. This ensures that only the user can access the website even if their credentials are at risk.
As far as Magento websites are concerned, the default 2FA is available without installing a third-party plugin. From the Magento Admin panel, there are four types of authentications that you can configure for an M2 store:
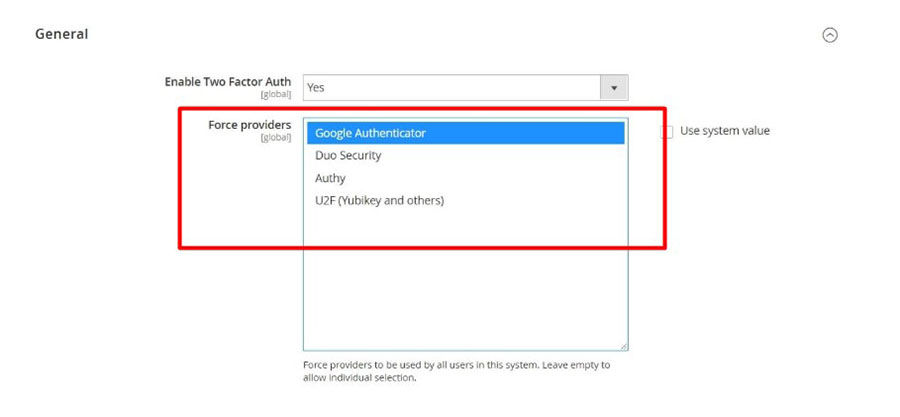
From the list of authenticators for M2 stores, you need to pick at least one of them per user account or force one for all accounts.
Read this step-by-step guide if you want to know how to enable 2FA on Magento.
Get Rid of Unused Extensions
Third-party plugins are potential entry points for intruders to penetrate websites. As such, loopholes in modules are often used by hackers to carry out SQL-injections or perform an XSS attack. Unused plugins and add-ons not only present a real threat to your website security but also negatively affect your store performance.
Thus, the first thing you have to do is to inspect your extension list. Then remove or disable components you don’t use. Depending on the platform you are using, the procedure may vary. To disable unused modules in Magento, you need to switch to SSH first and execute the following commands:
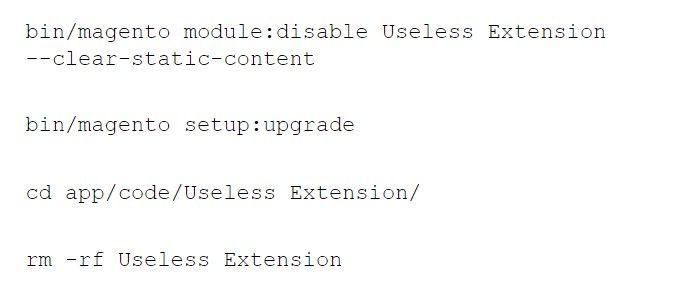
And don’t forget to make a backup before removal, just to be on the safe side.
Install SELinux to Boost Server Security
A correctly configured server environment is a great step toward a secure website. If your project is running on CentOS and Ubuntu, you can install SELinux to manage mandatory access controls, keep malicious content from affecting their vital data, and protect it against bugs in apps.
Enable reCAPTCHA in the Admin Panel
Even though many users find this practice boring and tedious (who wants to select all traffic lights in the image?), it remains one of the most effective ways to prevent password bruteforce. If your password is strong enough to withstand an assault, take into account that with each login attempt your server is getting more loaded. Which means longer processing time and slow performance for potential customers.
How can you enable a Storefront reCAPTHCA?
 Enable an SSL Certificate
Enable an SSL Certificate
An SSL certificate is a good way to secure your online store and create a trusted environment for potential shoppers making their transactions safe. In a nutshell, the certificate connects your website to security keys establishing an encrypted connection. When the key is installed on a server, it activates the HTTPS protocol that protects sensitive data while it is transmitting from a user to a website and vice versa.
In order to get an SSL certificate, you will need the following:
- You server certificate for your domain that is received from the CA after creating a CSR.
- An intermediate certificate that establishes the trust of your SSL certificate by allowing the devices connecting to your server to identify the CA.
- Your private key.
Install a Server Firewall
A server firewall is not only software for ensuring privacy and security through stopping unwanted connections that could cause data breaches. Besides, a firewall installed on a server is the best shield from malicious bots and DDoS attacks.
Basically, a firewall is a set of filters based on rules predefined by a user which aimed at restricting illegitimate traffic. By setting up firewall rules for a web server, a user can determine which packets are allowed to go through the firewall and which are not. Once a server identifies a traffic packet, it is subjected to the rule configured for the firewall. If the traffic is illegitimate, it is restricted.
Let’s assume that you’ve noticed that malicious bots are coming to your store from IPs belonging to a specific county, say, China. With a firewall rule, you can block all Chinese IPs, and hereby stop the attack of bad bots.
Build a Strong Backup System
Without a solid backup system, all the security measures are nothing. Despite all the efforts, your data can be compromised, your stuff can open an email infected with ransomware, or something else can malfunction. Backups are your plan B if the worst-case scenario comes true.
The fact is that your hosting provider can help you build a solid backup system. It is a common practice for a good hoster will backup your static data every 12-24 hours and keep it if things go wrong.
Regular automated backups have become a common feature for both VPS and cloud hosting providers. However, you shouldn’t fully rely on them and make your own backups on a regular basis. What does a solid backup system include? An ideal backup system consists of at least three separate locations:
- hoster’s storage
- separate storage created somewhere in the cloud
- a hard drive or a dedicated server where copies are kept.
If you don’t ignore these practices but follow them immediately, you will definitely turn your website into an “impenetrable fortress”.
Has your store ever been the victim of cyberattacks? How do you handle your website security woes? We look forward to hearing your personal experience in the comments below.







Contributed by Alex Husar
Updated on 13th September 2021