
2018 has come and gone with yet another batch of alarming reports of security breaches, data leaks, and virus mutations that should leave the average PC user concerned for their devices and safety. Staying ahead of personal data before it reaches unintended recipients means studying and understanding various software options created for privacy’s sake. Still, it can seem a daunting task from an outsider’s perspective.
Yet understanding privacy and safety between your computer or mobile device and the world around you only requires a few steps. We’ll be breaking down our recommendations to just a few programs for various devices that are easily accessible with a little learning on the part of the end user. Remember that no one piece of software will solve every problem; however, installing anti-virus software doesn’t keep your data private, and routing your connection through a virtual private network (VPN) doesn’t stop malware from creeping onto your devices. With that in mind, here’s some of our most often utilized software.
Virtual Private Networks
The core of good internet anonymity depends on running a virtual private network that essentially acts as a go-between that stands between your computer and the internet in an effort to disguise your internet traffic. VPN software essentially works by connecting you to a server which then forwards your traffic along with the traffic of other VPN users, making it appear as if the data is coming from a swarm of anonymous people rather than your easily traced IP address.
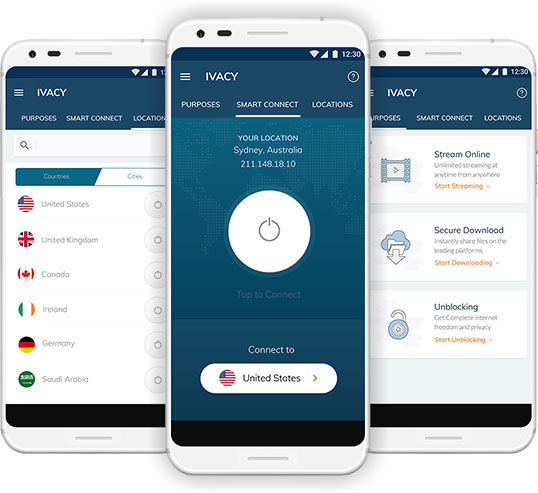
In order to be effective, a VPN provider needs to be secure, offer true anonymity, host multiple servers for better connection speeds, and allow mobile devices to connect through your account. As such, we recommend Ivacy, a service based out of Singapore that has operated for over a decade and continues to go on strong at every turn. At a price point that has reached as low as $60 USD for five years of service during its holiday sale, Ivacy’s strength and flexibility are difficult to beat.
With over 1,000 servers and dedicated apps for iPhone, Android, Xbox, Windows, Mac, Linux, and browser extensions for several popular options, flexibility is one of the company’s core concepts. You can use your Ivacy account across five separate devices instead of being tethered to just your PC or your phone. Staying private means keeping your data safe no matter what device is accessing it. Your phone can be one of the most easily compromised systems you carry, especially considering how many public networks you’re likely to access while using it. Thankfully, Ivacy’s VPN offers public Wi-Fi protection.
Yet the most important factor of any VPN is ensuring they do not keep logs of who accessed their servers or from which address those access requests originated. Ivacy keeps no logs, and its services are encrypted, making it harder to peek at your data.
Anti-Virus/Anti-Malware software
Keeping your digital fingerprint off of the internet at large is just the first step to staying safe. No privacy software can protect you if malware, viruses, or spyware has compromised your machine. While each variant has its own quirks and methods of attacking your system, all three can either hamper your PC’s performance, steal your data, or even ransoming data back to you after encrypting your hard drive. System security isn’t a matter to be taken lightly.
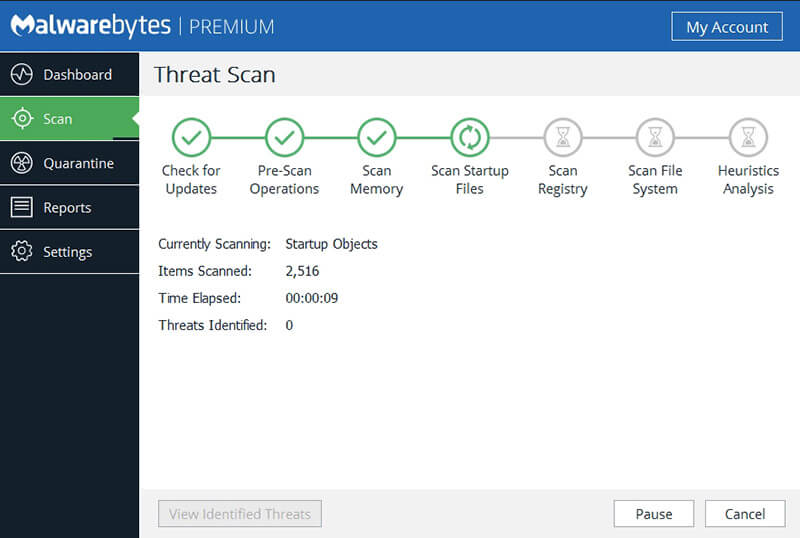
For general security needs, Malwarebytes has reigned supreme as the go-to response for virus and malware removal for the past several years. This crown is a heavy one, however, as the venerable software has reached a point where it seems a little too excited to prompt you to buy its premium services, but its free variant is a completely capable suite of anti-virus tools that sweep your drives for potential threats that you can then quarantine or delete appropriately. Best of all, they offer support for Windows, macOS, iPhone, and Android devices accordingly. In addition, if you step up to their paid service, you can monitor your devices in real-time to stop attacks before they happen.
If you only use Windows devices, the built-in Windows Defender is a surprisingly robust tool that performs as well as many free options on the market without a massive impact on your system and its performance. However, if you’ve ever had the unpleasant experience of using a PC running the Norton suite of anti-virus tools, you know all too well how badly an anti-virus program can choke the life out of a PC if it isn’t well designed.
Firewalls
Firewall programs operate simply: If a connection into or out of your device doesn’t seem right, the firewall stops the connection. The technical explanation is obviously more nuanced, but its essential function is to stop unwanted connections that could lead to breaches that introduce security vulnerabilities or data loss.
For Windows, the built-in firewall will handle most daily use applications without a problem, but you might consider stepping up to a program that can block on a program-by-program basis if you run many pieces of software that you suspect may not be as legitimate as they seem. For this purpose, Firewall App Blocker performs admirably. Blocking a program through the default Windows firewall takes several steps, but Firewall App Blocker lets you drag and drop the offending program to disable its internet access immediately. It’s also not susceptible to attacks that target the Windows firewall specifically, making it a nice secondary layer for the security conscious.
Mac machines also come with a capable firewall of their own, yet many machines have the firewall turned off by default. If you want more fine-tuned control, Little Snitch actively watches for network traffic and alerts you when certain programs ask for internet access so you can make real-time decisions rather than guessing whether a program will try to reach out through the internet or not.
Chat protocols
If most of your communication happens through common email protocols or chat programs, chances are you’re not anywhere near as secure as you could be. Many chat protocols, especially older ones, depend on legacy software that isn’t updated as often as it should be. Switching to a chat client that offers proper security options makes a big difference in ensuring the only people who see your messages are those you send them to directly.
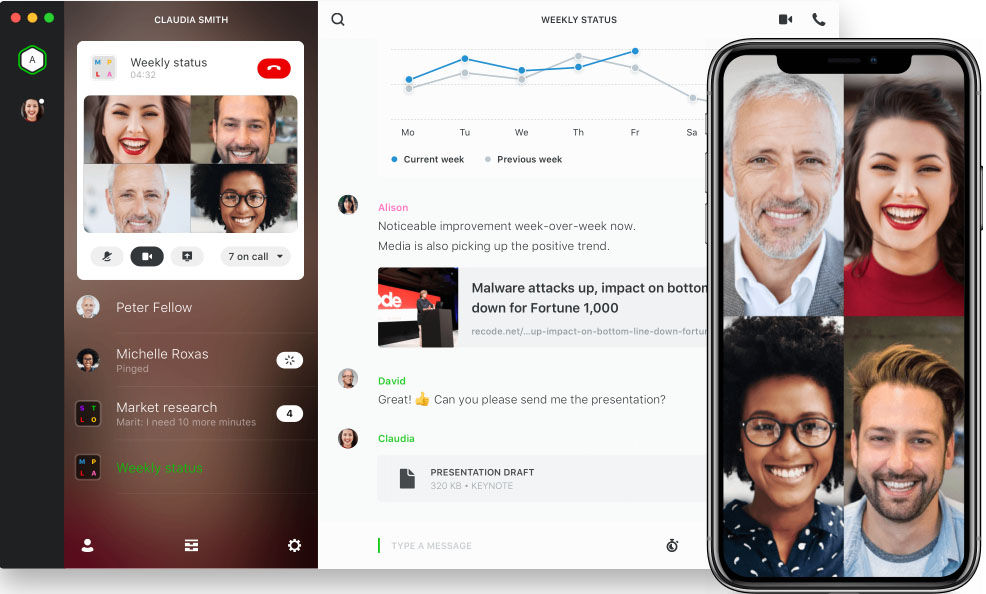
For this purpose, it’s difficult to recommend anything other than Wire. You can use safety plugins for other clients, but Wire was developed to be a secure multi-platform communication client that sports end-to-end encryption that makes it much more secure than many popular protocols. Wire supports text and video chat with the same levels of encryption and doesn’t require a phone number to register, and it’s free for personal use, though there is a paid option for professional or corporate users. It’s also ad-free, which points to its dedication to security and anonymity.
While the dream of sending secure emails is lovely, understanding email protocol vulnerabilities is vital in moving towards more secure options. It’s tempting to stick with an older form of communication that has been widely adopted. Unfortunately, the security failings of email have been under scrutiny for years, and even well-encrypted email messages can have incriminating metadata that may reveal information more revealing than the content of the email itself. If security is your concern, don’t rely on email as your primary form of communication.
Virtualization programs
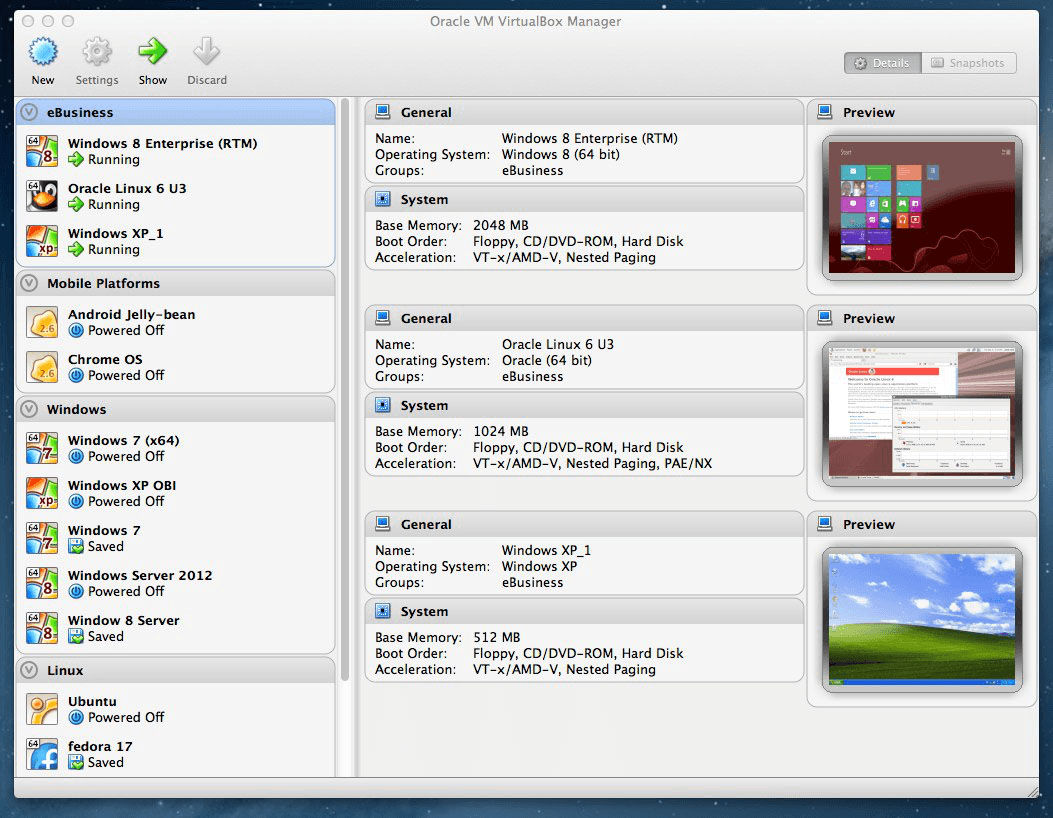
If you find yourself unimpressed with security software options, fear the risk of losing access to your machine, and have a bit of free time and a love for technology, virtualization is one of the strongest safeguards you can put in place. Essentially, virtualization programs allow you to run a virtual machine inside your computer that emulates an operating system in its own safe environment. If your VM is compromised, the computer running it is safe from infection as long as no files are transferred between them.
There are several options, and each program focuses on emulating a certain type of machine. For instance, VirtualBox seeks to emulate Intel and AMD-based systems running Windows, Linux, or even DOS if you should find yourself pining for the old days. One of its most useful boons is being able to emulate a Windows PC while running the VM software on your macOS or Linux device, meaning you can run Windows without having to use it every day, yet you don’t lose out on flexibility in the suites of programs you have available to you. You can even install a virtual Android operating system if you’d like to test phone apps out without installing them on your physical phone.
Much like before, it is important to note that a VM isn’t a guarantee of safety. If you accidentally download a virus that can access your network, it can use that access from inside your virtual box to wreak havoc through even the most secure virtual machine. If you’re truly concerned about a program you intend to install, install it on a machine that has no internet access that you don’t use regularly. While an inconvenience, it may save you a lot of trouble and pain in the long run.
How to pick out anonymous browsers and excellent privacy tools?
Before choosing the best anonymous browsers and privacy tools, it is important to review the required features. It includes the server speeds and locations, the encryption level, the platforms the tools run on, monthly data limits, and the number of devices on which it can be used at a time.
If your main goal is to unblock sites, then you should check whether the tool can unblock desired sites. Along with the pricing plan, you should also consider the user-friendly interface and ease of setting up the tool.
How did we test the best privacy tools?
We tested a wide variety of tools to find the best anonymous browsers and privacy tools. We take into account their pricing plans, server speeds and locations, encryption strength, monthly data limits, platforms they support, and the number of devices they can be used on simultaneously.
We reviewed the user-friendly interface and installation and assessed how easily the tool could be set up. Along with speed and performance, we also consider how many geo-restricted sites it can unblock. We also checked whether tools have a clear no-ads and no-logging policy that deleted all data.
Taking security seriously
Keeping unwanted individuals from accessing your data takes a level of vigilance and care that many of us take for granted these days. It’s not fun to set up a virtual machine just to keep a suspicious file from infecting our main computer, but taking the time necessary to protect your data before it gets out into the wild is often easier than trying to play damage control after the fact. If you feel nervous about the websites you visit or think a program might harm your computer, don’t just act as you normally do. Take the time to investigate its origins and find out how dangerous it may actually be.
Above all, paying attention and working safely will save you from a headache nine times out of ten. For every other incident, you’ll thank yourself for setting up a VPN and not sending sensitive information through unencrypted email services. For further reading, check out our guide on surfing the web anonymously and stay safe above all else.







This article is brought to you by Andrej Kovacevic
Updated on 1st August 2022